Depending on the pentest given (whitebox/greybox/blackbox) you may or may not have a scope. For these examples, I’ll be under the assumption I have a scope from the customer for their domain, corp.local which runs under the 192.168.1.0/24 network. For these examples, I have my ESXI server running four VMs:
Windows Server 2008 R2 (Primary DC)
Windows 7 (Workstation)
Windows Server 2003 (Secondary DC)
Windows XP (Unpatched; Workstation)
My initial scan reveals the four machines and their IPs. The workstations look like they might have old software with exploitable vulnerabilities, however I want to try and see what credentials I can find on the network before resulting to traditional exploits like buffer overflows. To do this, I’ll be using a tool called Responder to exploit LLMNR and NBT-NS if the network is configured to use those protocols (Usually on by default). To summarize what they do, when you type in a network share, say \\Fileserver01\, but it doesn’t exist, by default Windows will send out a LLMNR broadcast across the network to see if anyone knows where it is. If that fails, it then uses NBT-NS. When that fails, you get the error message saying the share cannot be found. But, by using Responder, we broadcast spoofed LLMNR and NBT-NS responses by saying “yeah, that share exists, what’s your username and password?” which is then passed to Responder, but the password is an NTLMv2 hash.
Here it is in action:
By default, Kali has Responder installed already, so all you need to do is type
responder -I eth0
Or whatever interface you’re using.

Next, is to simulate a user mistyping a share.
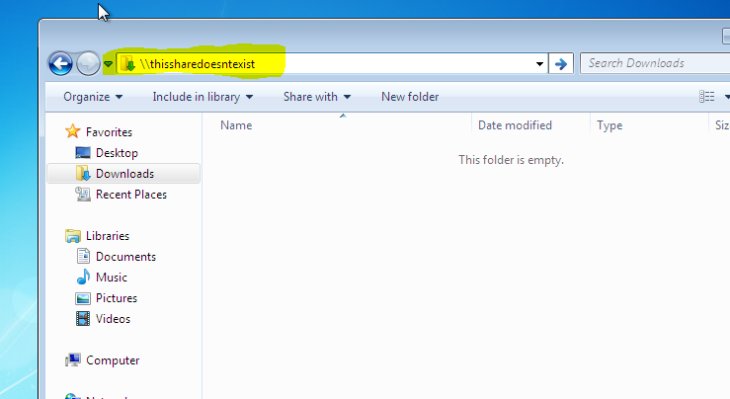
And we now see the LLMNR request in responder

And a short while later we get the user’s hashed credentials:

NTLMv1/2 hashes cannot be passed. Regular NTLM hashes can, but if it’s v1/v2 it cannot. So we have two options:
- We can crack it
- We can relay it using a tool like ntlmrelayx.py
Cracking is always a viable option anyways but doesn’t always work, especially if the group policy enforces a strong password. For relaying, you can read my write-up here, but for this write up, I will just crack it. I personally like Hashcat since it can utilize my GPU.
Note: I have hashcat installed on Windows
Cracking the Hash via Hashcat
By default, the hash is stored in /usr/share/responder/logs
Using the command
hashcat64.exe -m 5600 hash.txt password.txt -o results.txt
Where “hash.txt” is my hash and “password.txt” is my wordlist and “results.txt” is my output file. -m 5600 is for the hash type, which is NTLMv2.
Shortly after running the command, the password is cracked.

From here I could then RDP into the machine and do as I please, or use it to enumerate other machines, which is shown in my post here.